As a security officer with an SIA licence, whether trained in trained in door supervision, security officer roles, or CCTV operations, your role is crucial in maintaining physical security. However, in our digital age, it’s equally important to be aware of cyber security threats. Most threats today happen digitally, making it essential for security officers to understand and identify these risks. This knowledge not only enhances your skill set but also helps you better protect the premises and assets under your care.
Understanding Key Cyber Security Threats
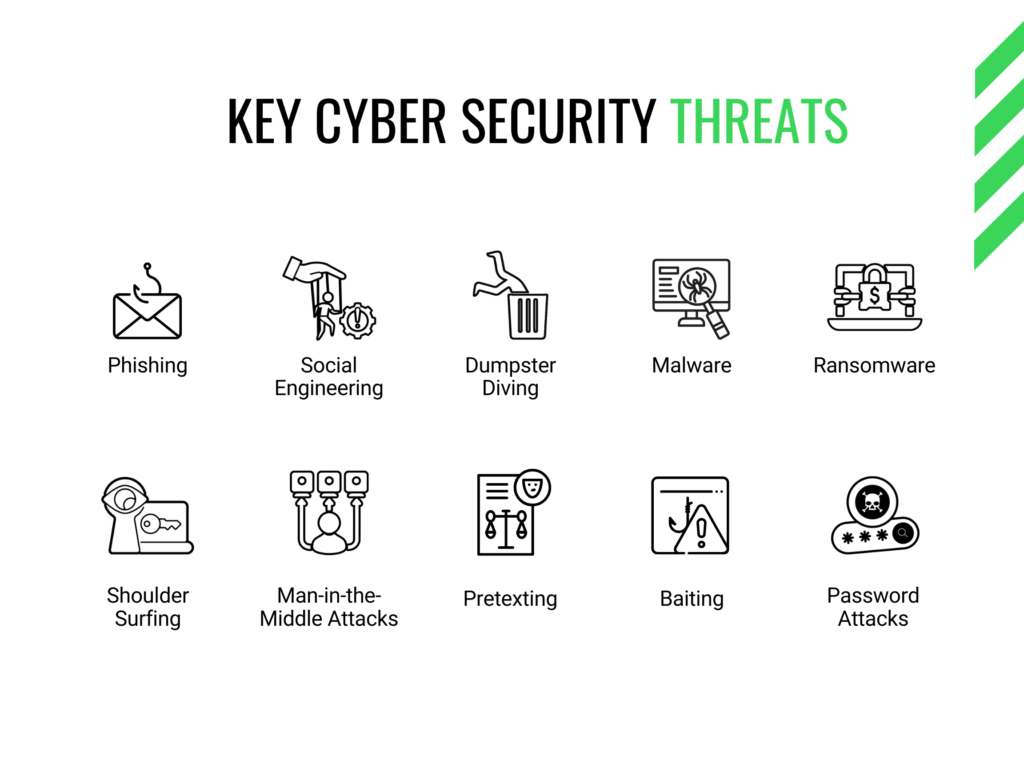
Here are the top 10 cyber security threats every frontline officer should know:
1. Phishing
Phishing is a scam where attackers send fake emails or messages that look like they’re from legitimate sources, such as banks or companies. These messages often contain links or attachments that, when clicked, can steal your personal information or infect your computer with malware. As a security officer, be cautious of unsolicited emails and always verify the sender before clicking on any links.
2. Social Engineering
Social engineering involves manipulating people into giving away confidential information. Attackers may pose as colleagues or authority figures to gain your trust and trick you into divulging sensitive information. Always verify the identity of the person requesting information and never share personal or company details unless you’re certain of their authenticity.
3. Dumpster Diving
Dumpster diving is a technique where attackers search through trash to find sensitive information that hasn’t been disposed of properly. Ensure all documents containing personal or company information are shredded before disposal to prevent attackers from accessing valuable data.
4. Malware
Malware, or malicious software, is designed to harm or exploit any programmable device or network. It can come in the form of viruses, worms, Trojan horses, ransomware, or spyware. Always keep your software and antivirus programs updated to protect against malware.
5. Ransomware
Ransomware is a type of malware that locks your files or system, demanding payment for their release. Never pay the ransom, as it doesn’t guarantee you’ll get your data back. Instead, focus on prevention by backing up your data regularly and keeping your security software up to date.
6. Shoulder Surfing
Shoulder surfing is a low-tech method where attackers simply watch over your shoulder as you enter passwords or other sensitive information. Be aware of your surroundings and use privacy screens if necessary to protect your information from prying eyes.
7. Man-in-the-Middle Attacks
In a man-in-the-middle attack, an attacker secretly intercepts and relays messages between two parties who believe they are directly communicating with each other. Ensure you’re using secure, encrypted connections when transmitting sensitive information.
8. Pretexting
Pretexting is a form of social engineering where an attacker creates a fabricated scenario to steal your information. For example, they might pretend to be from IT support and ask for your login credentials. Always verify the identity of anyone requesting personal or sensitive information.
9. Baiting
Baiting involves enticing victims with something appealing, like a free download or USB drive, which contains malicious software. Avoid using untrusted USB drives and only download software from reputable sources.
10. Password Attacks
Password attacks involve hackers trying to gain access to your accounts by cracking or guessing your passwords. Use strong, unique passwords for each of your accounts and change them regularly. Consider using a password manager to keep track of your passwords securely.
Enhancing Your Skills
Understanding these common cyber security threats is the first step in protecting yourself and your organisation. While this knowledge is valuable, consider enhancing your skills further with a basic cyber security course.
At Get Licensed, we offer an excellent e-learning course that can help you get started. Our courses are designed to empower you with the latest knowledge and skills needed to stay ahead in the security industry. Join our community of professionals dedicated to maintaining the highest standards of safety and security.
Conclusion
As a security officer, your role in physical security is vital, but being aware of digital threats is equally important. By understanding and recognizing these common cyber security threats, you can enhance your capabilities and provide comprehensive protection. Effective security strategies often require a seamless integration of both physical and digital measures, highlighting how the best cybersecurity practices often rely on solid physical security. Remember, physical security is an extension of cyber security. Stay informed, stay vigilant, and stay secure.







Leave a Reply